Analysis: Spam Header
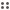 Email header: where the spam starts Email header: where the spam starts
Here is the starting part of the header of a junk email (spam), which includes information about the transfer of the email between the sender and the receiver:

Let's analyze the red highlighted lines:
Return-path: the header tells that if you reply to this email message, the reply will be sent to ydcdd...@yahoo.com. Would you use such an email address for real?
Received tags: as on web blogs, read them from the bottom to top. The header says the email was originally sent from 206.85... and it was sent to 217.225... (which is the name/IP of the first mail server that got involved into transporting this message). Then suddenly, the next Received tag says the message was received from root@localhost, by mailv.fx.ro. You can also notice that so far, the Received tags do not contain any information about how the email was transmitted (the "with" tag is missing: this tag tells the protocol used to send the email).
In reality, this is the common case of a spammer pretending to be the root user of mailv.fx.ro and sending the email from 206.85..., through 217.225... and telling 217.225... to act as the root user of mailv.fx.ro, in order to use the SMTP server of mailv.fx.ro to send the email. Since more and more mail servers are not allowing open-relay connections, the spammer can only use the mail server of the receiver, in order to send the message. If the spammer will try to send the email to support@emailaddressmanager.com, through exactly the same route as above, it wouldn't work, because support@emailaddressmanager.com is not a network user of mailv.fx.ro. This is the reason why you may have received spam emails appearing to be sent through an email address of your own ISP.
Going deeper with the analysis, you can use an IP tracing tool, like Visual Route, in order to see to whom the IP belongs to. As in most of the spamming cases, the starting IP (206.85...) is unreachable, which means that the spammer could have routed the real IP or he could have used a dynamic IP (a normal case for dial-up users). However, by tracing 217.225..., you will get to the ISP used by the spammer, a German provider. The ISP has nothing to do with the spam itself, but it was simply used by the spammer to connect to the Internet.
Let's look further into the email header:
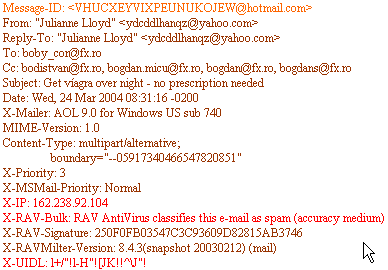
The Message-ID field is a unique identifier of each email message. It is like the tracing ID of an express postal mail. The rule says the ID is composed by the name of the server that assigned the ID and a unique string (for example, QESADJHO@emailaddressmanager.com). Hmm, this is strange, because on our case, the ID belongs to hotmail.com, while the sender appears to belong to yahoo.com. In fact, this difference mainly shows that the sender is forged (fake address or someone pretending to own that email address).
The X-IP tag (also named X-Originating-IP) is probably the most important one and it should give precise information about the sender (from where the email was actually sent). Unfortunately, this tag is optional for email protocols, so some spam messages will not include it. As you can see, the originating IP is not even close to the sender's IP, from the Received tags.
The X-UIDL tag is another unique ID, but this one is used by the POP3 protocol when your email client is receving the email. This is an optional email tag, but the rule of thumb says spammers love to include it.
Visual comparison between a spam email header and a normal email header.
Back to the Email Tips Index.
|
|
|

